OWASP 2021 Detailed Report: See What’s Changed!

Everyone knowing about OWASP must be curious about what's modified withinside the Top 10 for 2021.
Here’s What’s New in the Top 10 for 2021
There are three new classes, four classes with naming and scoping changes, and a few consolidations with the Top 10 for 2021. They have modified names while essential to acknowledge the core reason of the symptom.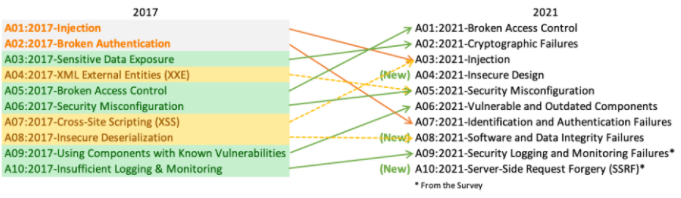
Image Source: https://owasp.org/Top10/
A01:2021-Broken Access Control goes up from the fifth situation to the category with the most genuine web application security risk; the contributed data indicates that on average, 3.81% of applications tried had one or more normal Weakness Enumerations, i.e., CWEs with more than 318k instances/occurrences of CWEs in the same risk category. These 34 CWEs mapped to Broken Access Control had a larger number of occurrences in applications than any other category.
A02:2021-Cryptographic Failures shifts up one situation to #2, recently known as A3:2017-Sensitive Data Exposure, which was a broad indication rather than an underlying driver. The restored name centers around failures related to cryptography, as it has been certainly previously. This category frequently leads to system compromise or sensitive data exposure.
A03:2021-Injection comes down to the third position. 94% of the applications were tried for some type of injection with a maximum incidence rate of 19% and an average incidence rate of approx. 3.37% with 33 CWEs mapped into the same category have the second most instances/occurrences in applications with 274k occurrences. Cross-site Scripting is presently part of this category in this version.
A04:2021-Insecure Design is another category for 2021, with attention on risks related to design flaws. If we really want to "move left" as an industry, we wanted more threat modeling, secure design patterns and standards, and reference architectures. An insecure design cannot be fixed by an ideal implementation as, by definition, required security controls were never created to protect against explicit attacks or risks.
A05:2021-Security Misconfiguration exceeds from #6 in the past release; 90% of applications were tried for some sort of misconfiguration, with an average rate of 4.5% & over 208k occurrences of CWEs mapped to the same risk category. With more moves into profoundly configurable software, it's not unexpected to see this category move up. The previous category for A4:2017-XML External Entities (XXE) is presently part of this risk category.
A06:2021-Vulnerable and Outdated Components was recently named Using Components with Known Vulnerabilities and are #2 in the Top 10 local area study, yet additionally had sufficient data to obtain the Top 10 while using data analysis. The respective category goes up from #9 in 2017 and is a recognized issue that we battle to test plus assess risk. It is the main category without any Common Vulnerability & Exposures (CVEs) getting mapped to the inclusive CWEs; that's why a default exploit and impact loads of 5.0 are factored into their scores.
A07:2021-Identification and Authentication Failures was recently Broken Authentication is coming down from the subsequent position, and presently incorporates CWEs that are more related to identification failures. This category is as yet an integral part of the Top 10, yet the increased availability of standardized frameworks is by all accounts making a difference.
A08:2021-Software and Data Integrity Failures is another category for 2021, zeroing in on considering assumptions concerning software updates, critical data & CI/CD pipelines with no checking integrity. One of the greatest weighted impacts from CVE/CVSS (Common Vulnerability and Exposures/Common Vulnerability Scoring System) data mapped to the 10 CWEs in this category. A8:2017-Insecure Deserialization is presently a part of this larger category.
A09:2021-Security Logging and Monitoring Failures was beforehand A10:2017-Insufficient Logging and Monitoring and is added from the Top 10 local area overview (#3), climbing from #10 already. This category is expanded to incorporate more kinds of failures, is challenging to test for, and isn't all around addressed in the CVE/CVSS data. Be that as it may, failures in this category can straightforwardly impact permeability, forensics, incident alerting.
A10:2021-Server-Side Request Forgery adds to the Top 10 local area overview (#1). The data reveals a comparatively low incidence rate with over average testing coverage, including above-average ratings for Impact & Exploit potential. This category addresses the scenario where the security local area individuals are letting us know this is important, despite the fact that it's not illustrated in the data at this time.


