Kubernetes Security: Build Phase
| Overview : |
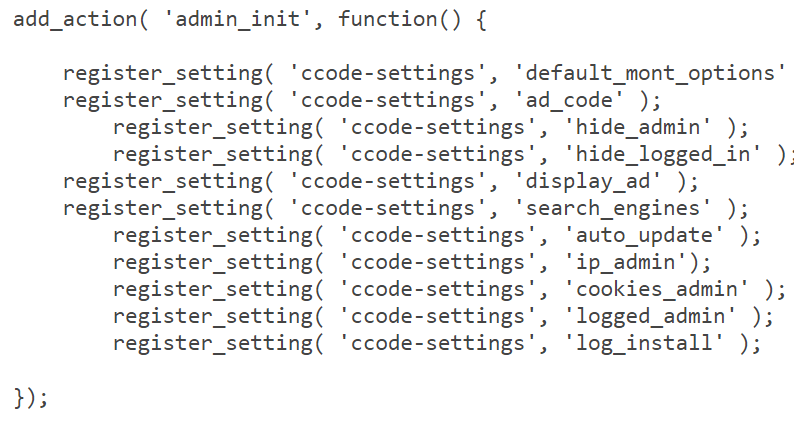
Kubernetes Security: Build PhaseSecuring containers and Kubernetes starts within the building part with securing your container images. Your time spent right here pays dividends later due to the fact any neglected protection excellent practices at this factor may be considerably greater luxurious to restore down the line – as a result the phrase “shift left” which means enforcing protection at in advance ranges as images are built. The two important things to work with this phase are to create secure images and to scan those images for any familiar vulnerabilities. |